Provide access to your team
There are 2 very important notions:
- service owners which is a list of thalesian that have the right to give access to k8saas instance
- users which is a list of thalesian that have access to k8saas instance (but haven't the permission to give access)
To provide an access to a thalesian, you should be part of the service owner of your cluster. By default, the requester is service owner
Add service owner access
Using Azure Portal
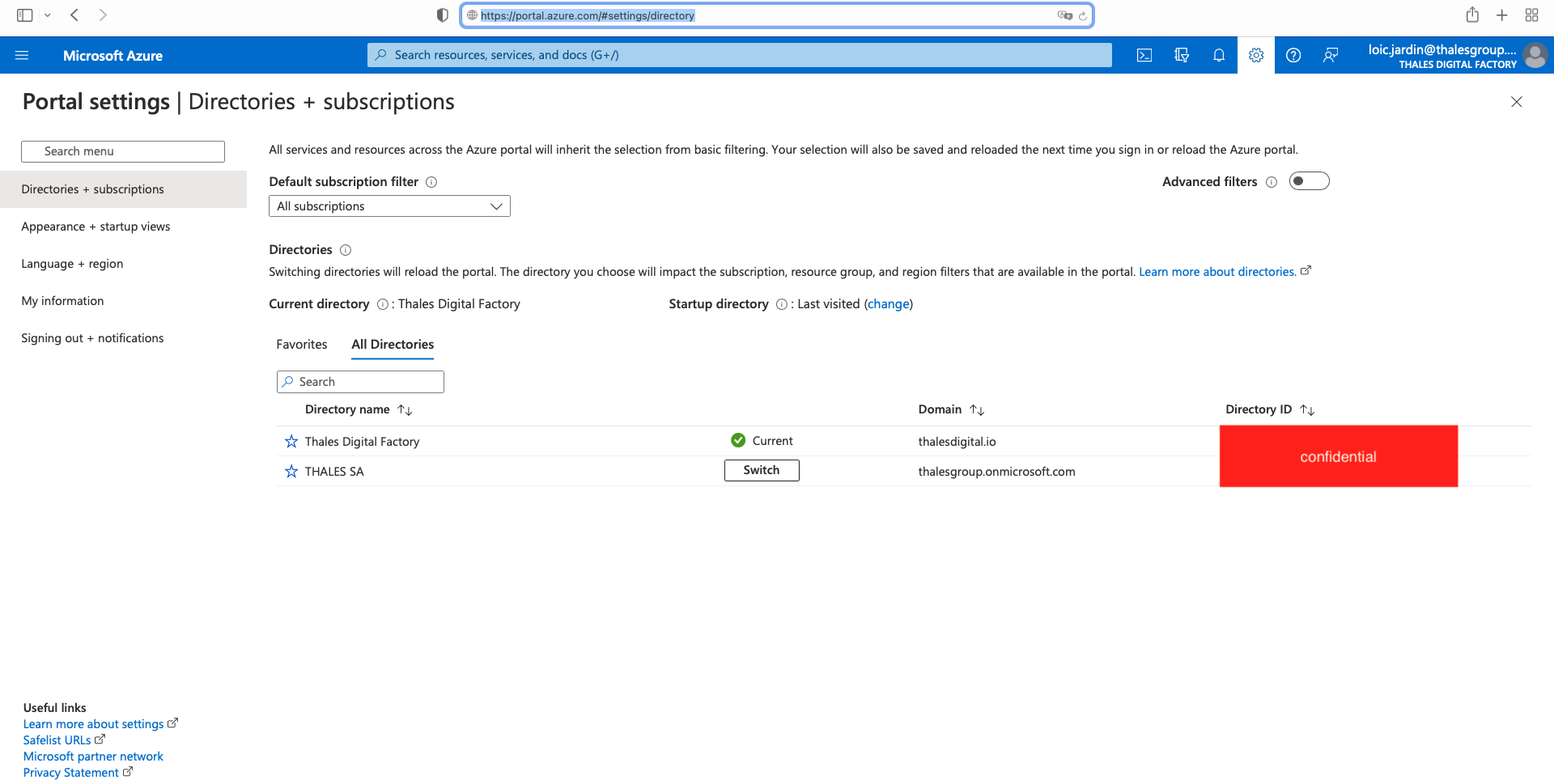
First go to https://portal.azure.com and log in using the identity provided in the cluster creation form.
Then make sure you are in the right Directory Name using https://portal.azure.com/#settings/directory . Use the K8SAAS_TENANT_ID provided by email.
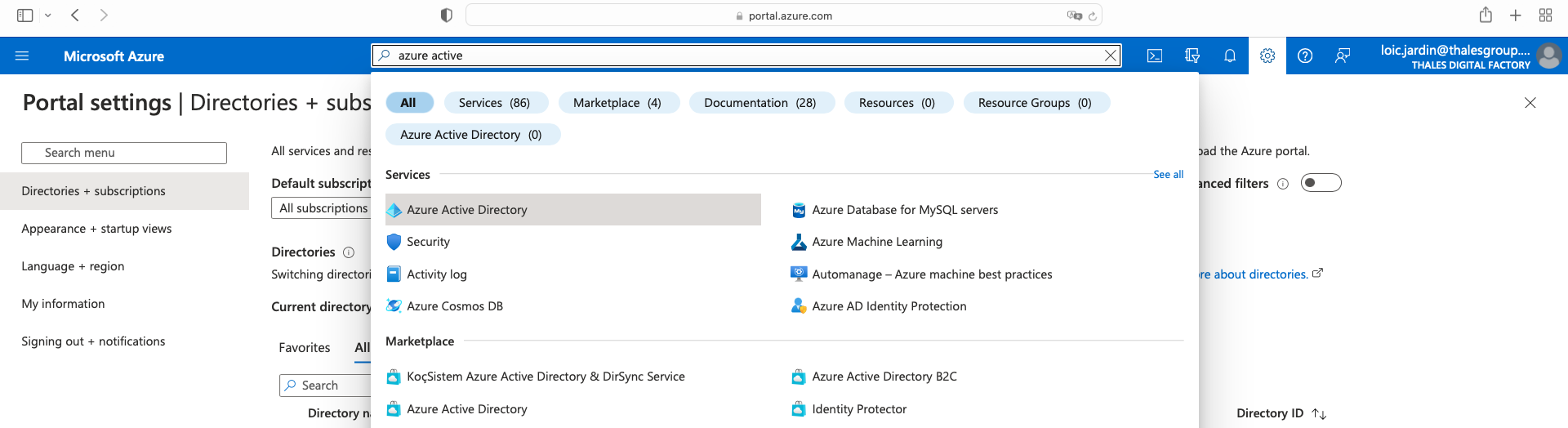
Then, in the search bar, on the top, search for Azure Active Directory
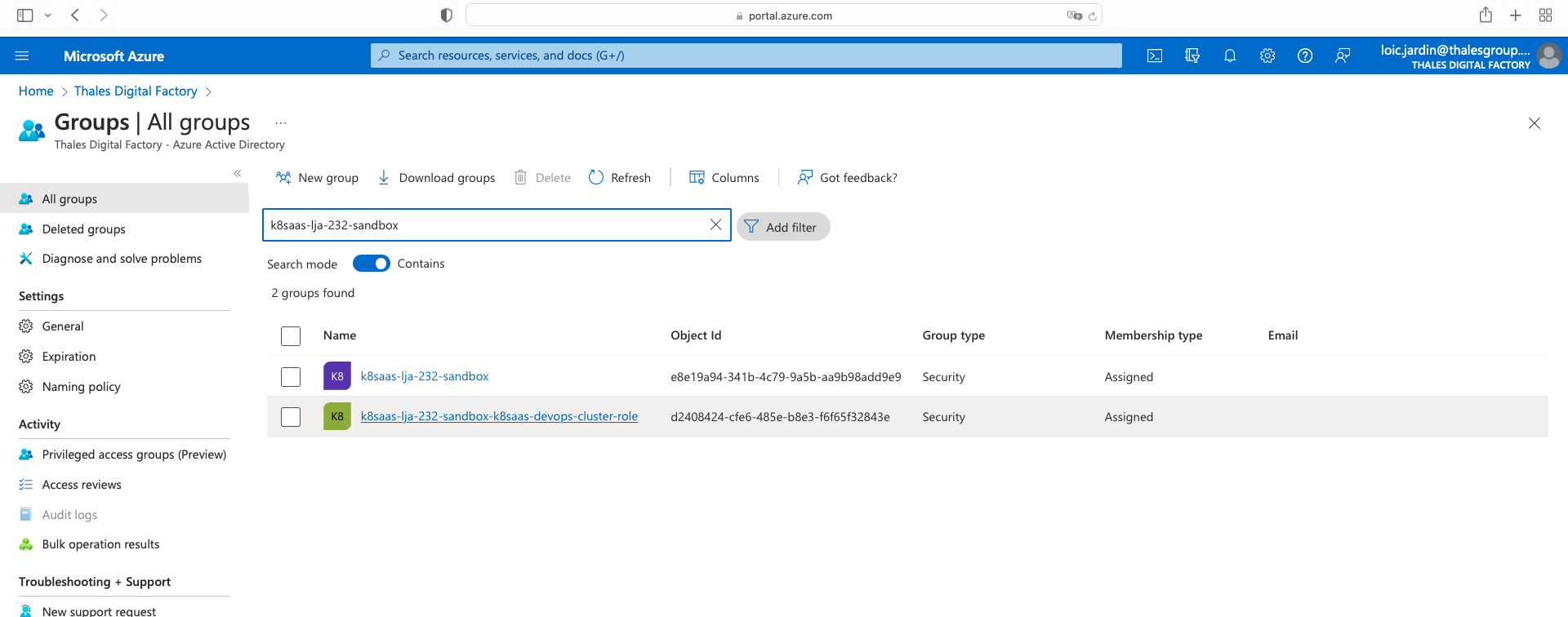
Select groups, and search for K8SAAS_RESOURCE_NAME (provided by email), you should see several groups. Select the group suffixed by "devops-cluster-role".
In the following example:
- K8SAAS_RESOURCE_NAME is k8saas-lja-232-sandbox
then,
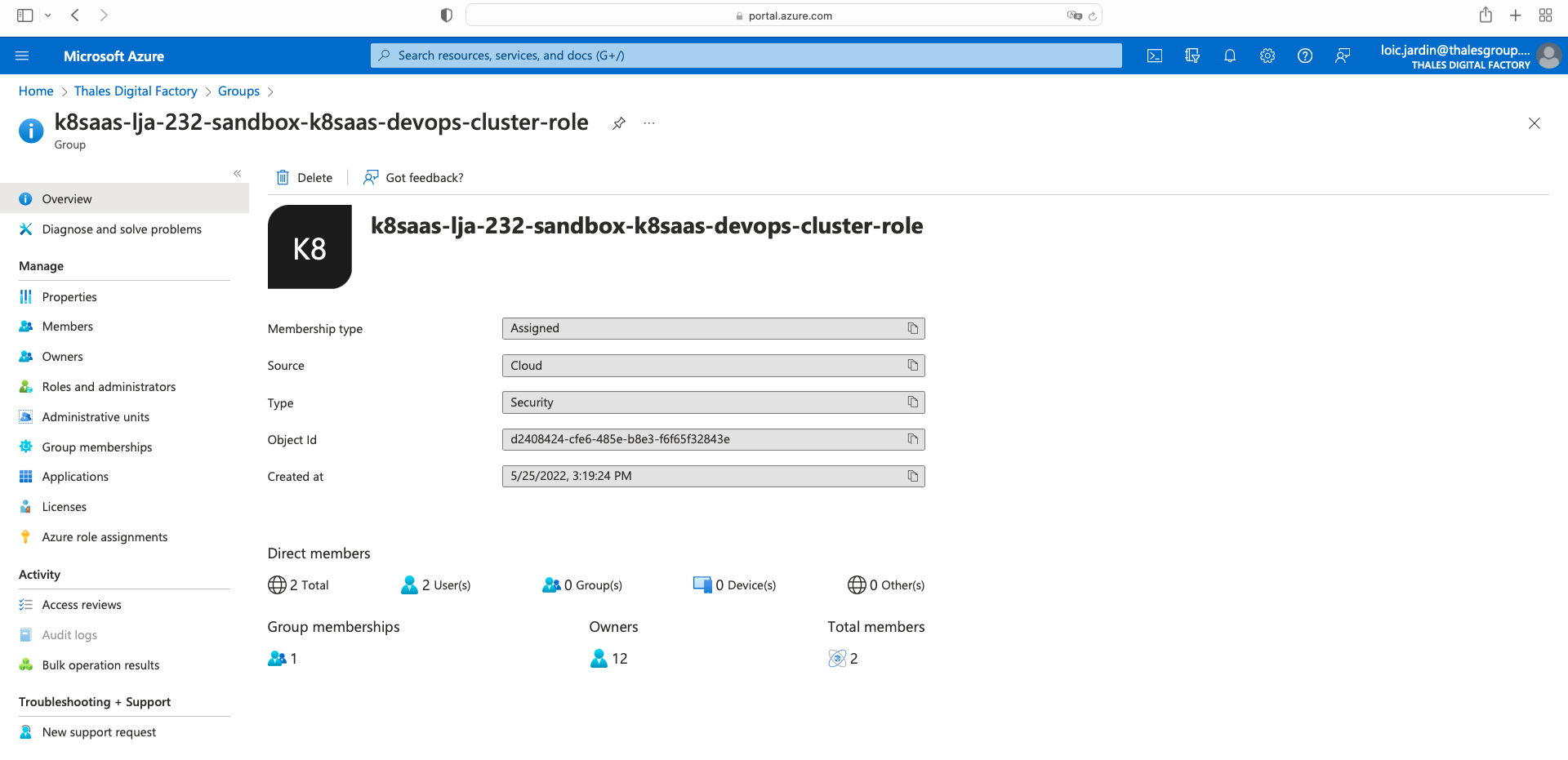
Click on owners tab on the left, then Add owners, and finally click on "Select"
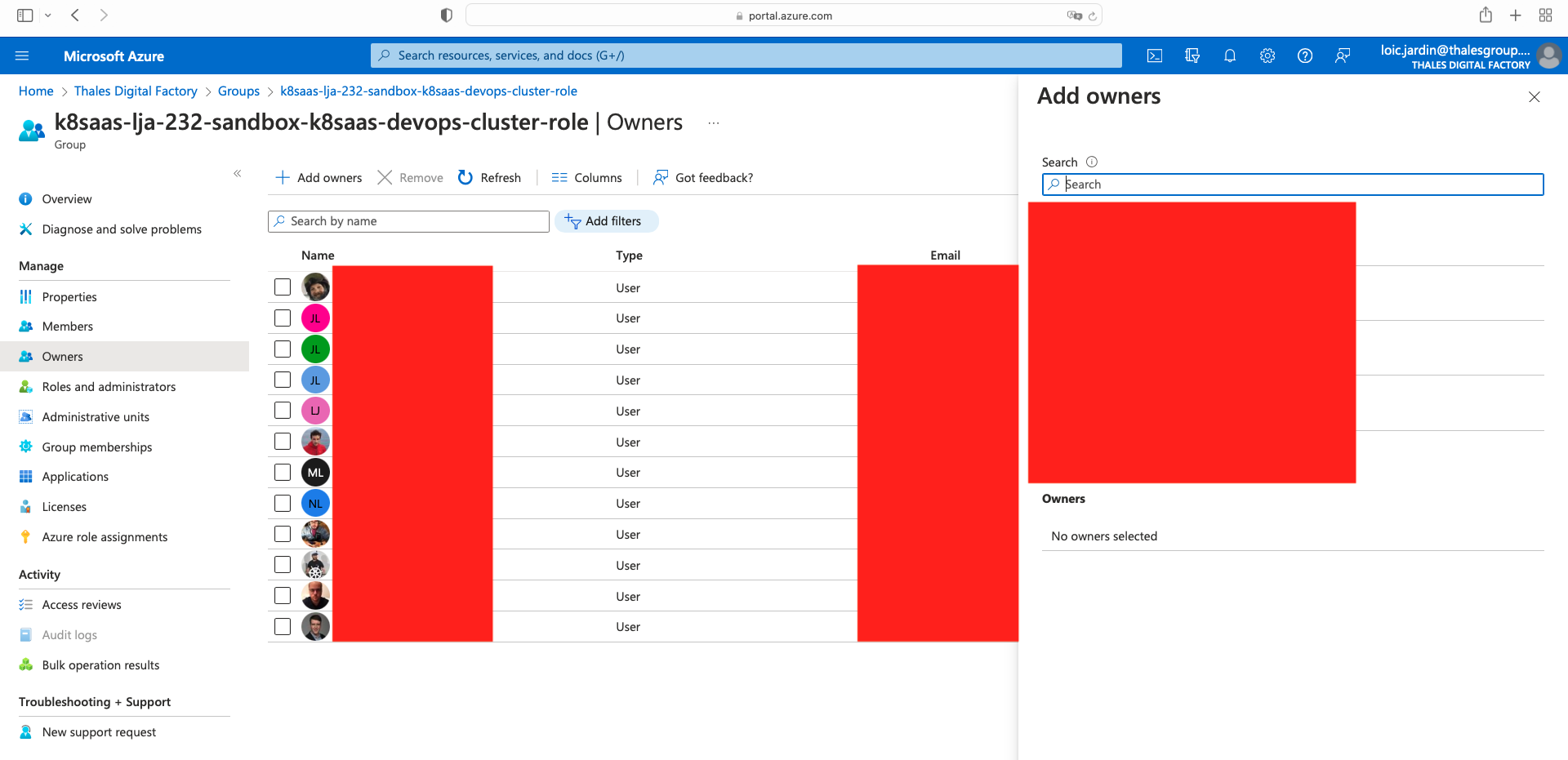
Reader group is not available by default. If reader group is shown from the groups list, you need to repeat the steps for the devops group on the reader group.
Using Azure CLI
First make sure you are logged in the right tenant. The output of the following command must contains the K8SAAS_TENANT_ID. If not re do az login -t "$K8SAAS_TENANT_ID"
az ad signed-in-user show -o json|jq '."odata.metadata"'
Identify the thalesian email address you want to add, and put in NEW_SERVICE_OWNER_EMAIL_ADDRESS
NEW_SERVICE_OWNER_EMAIL_ADDRESS="my_email@thalesdigital.io"
az ad group owner add --group $K8SAAS_RESOURCE_NAME-k8saas-devops-cluster-role --owner-object-id $(az ad user show --id $NEW_SERVICE_OWNER_EMAIL_ADDRESS -o json|jq -r '.id')
for thalesgroup: firstname.lastname_thalesgroup.com#EXT#@thalesdigital.onmicrosoft.com for thalesdigital.io: firstname.lastname@thalesdigital.io
Check if the previous command has been process, you see a line containing NEW_SERVICE_OWNER_EMAIL_ADDRESS
az ad group owner list --group $K8SAAS_RESOURCE_NAME-k8saas-devops-cluster-role -o json|jq '.[].userPrincipalName'
Reader group is not available by default. If reader group is shown from the groups list, you need to execute the following commands to also add the new owner as owner in the reader group.
az ad group owner add --group $K8SAAS_RESOURCE_NAME-k8saas-reader-cluster-role --owner-object-id $(az ad user show --id $NEW_SERVICE_OWNER_EMAIL_ADDRESS -o json|jq -r '.id')
Check if the previous command has been process, you see a line containing NEW_SERVICE_OWNER_EMAIL_ADDRESS
az ad group owner list --group $K8SAAS_RESOURCE_NAME-k8saas-reader-cluster-role -o json|jq '.[].userPrincipalName'
Add user access
| Role | Access | Availability |
|---|---|---|
| K8SAAS_RESOURCE_NAME-devops-cluster-role | Has read/write access on resources in customer | By default |
| K8SAAS_RESOURCE_NAME-reader-cluster-role | Has readonly access on resources in customer | On request |
Using Azure Portal
First go to https://portal.azure.com and log in using the identity provided in the cluster creation form.
Then make sure you are in the right Directory Name using https://portal.azure.com/#settings/directory . Use the K8SAAS_TENANT_ID provided by email.

Then, in the search bar, on the top, search for Azure Active Directory

Select groups, and search for K8SAAS_RESOURCE_NAME (provided by email), you should see several groups. Select the group suffixed by "devops-cluster-role".
Reader group is not available by default. To provide reader access to your cluster, select the group suffixed by "reader-cluster-role" and follow devops steps.
In the following example:
- K8SAAS_RESOURCE_NAME is k8saas-lja-232-sandbox

then,

Click on Members tab on the left, then Add members, and finally click on "Select"
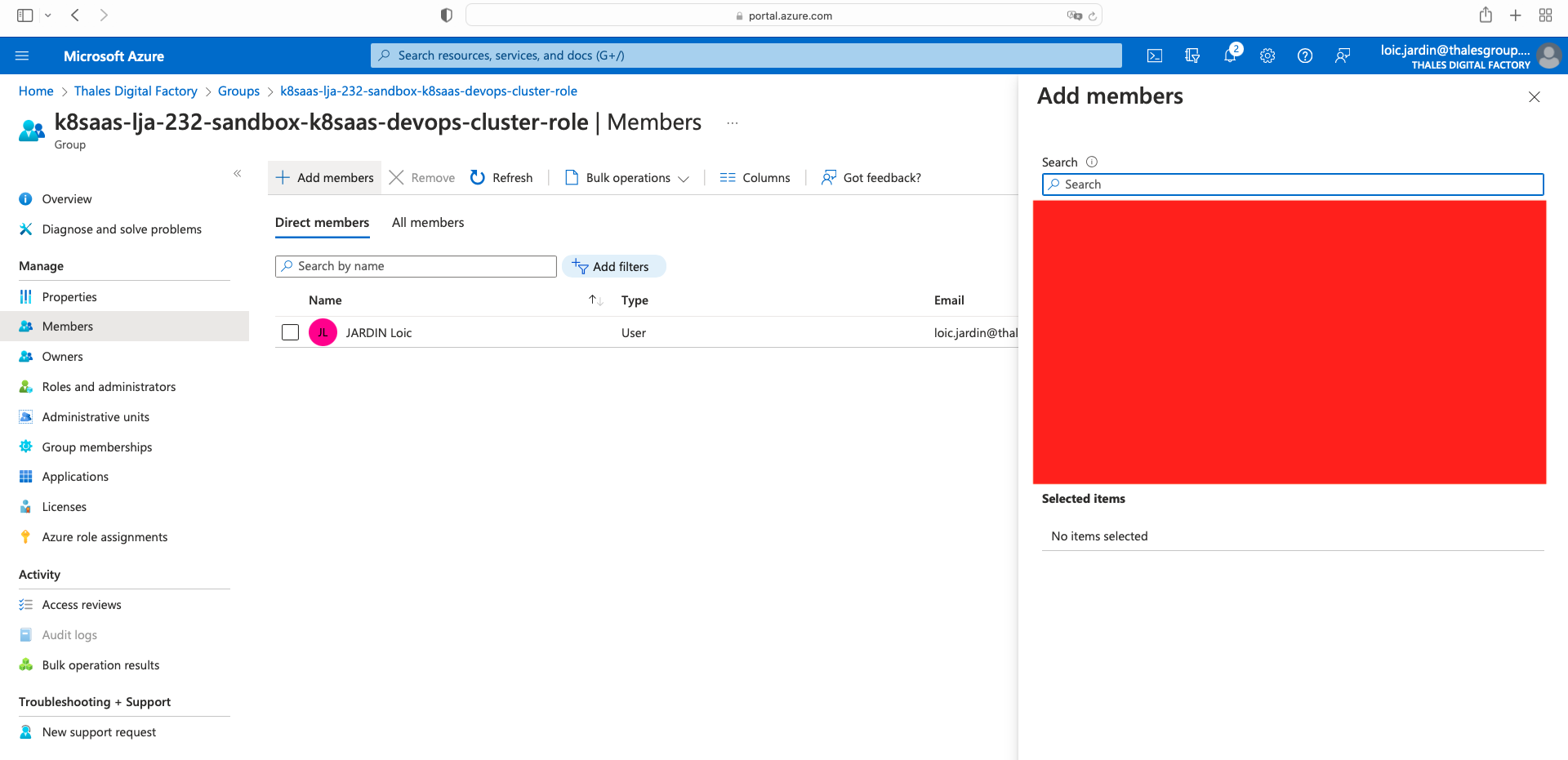
Using Azure CLI
Add devops user
First make sure you are logged in the right tenant. The output of the following command must contains the K8SAAS_TENANT_ID. If not re do az login -t "$K8SAAS_TENANT_ID"
az ad signed-in-user show -o json|jq '."odata.metadata"'
Identify the thalesian email address you want to add, and put in NEW_SERVICE_OWNER_EMAIL_ADDRESS
NEW_DEVOPS_EMAIL_ADDRESS="my_email@thalesdigital.io"
az ad group member add --group $K8SAAS_RESOURCE_NAME-k8saas-devops-cluster-role --member-id $(az ad user show --id $NEW_DEVOPS_EMAIL_ADDRESS -o json|jq -r '.id')
for thalesgroup: firstname.lastname_thalesgroup.com#EXT#@thalesdigital.onmicrosoft.com for thalesdigital.io: firstname.lastname@thalesdigital.io
Check if the previous command has been process, you see a line containing NEW_DEVOPS_EMAIL_ADDRESS
az ad group member list --group $K8SAAS_RESOURCE_NAME-k8saas-devops-cluster-role -o json|jq '.[].userPrincipalName'
Add reader user
Reader group is not available by default on cluster. If require, please create a request on PostIT
First make sure you are logged in the right tenant. The output of the following command must contains the K8SAAS_TENANT_ID. If not re do az login -t "$K8SAAS_TENANT_ID"
az ad signed-in-user show -o json|jq '."odata.metadata"'
Identify the thalesian email address you want to add, and put in NEW_SERVICE_OWNER_EMAIL_ADDRESS
NEW_READER_EMAIL_ADDRESS="my_email@thalesdigital.io"
az ad group member add --group $K8SAAS_RESOURCE_NAME-k8saas-reader-cluster-role --member-id $(az ad user show --id $NEW_READER_EMAIL_ADDRESS -o json|jq -r '.id')
for thalesgroup: firstname.lastname_thalesgroup.com#EXT#@thalesdigital.onmicrosoft.com for thalesdigital.io: firstname.lastname@thalesdigital.io
Check if the previous command has been process, you see a line containing NEW_READER_EMAIL_ADDRESS
az ad group member list --group $K8SAAS_RESOURCE_NAME-k8saas-reader-cluster-role -o json|jq '.[].userPrincipalName'
Grafana access
We reviewed the way we onboard user on Grafana, by adding user to k8saas AAD groups shown in the upper section of this documentation each user will be attach to a role in Grafana automatically.
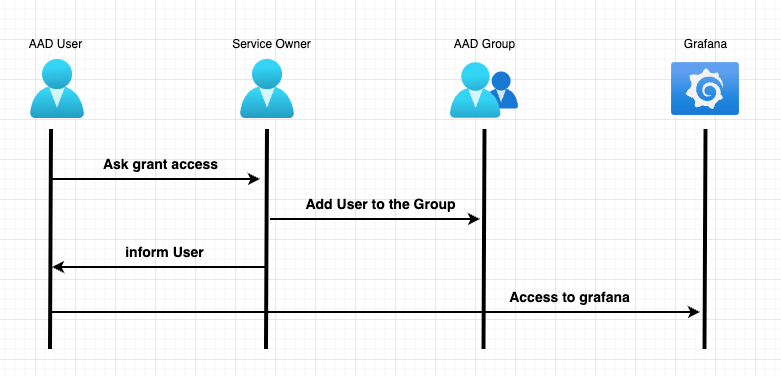
The AAD group $K8SAAS_RESOURCE_NAME-k8saas-devops-cluster-role & $K8SAAS_RESOURCE_NAME-k8saas-developer-cluster-role will have the role Editor. While $K8SAAS_RESOURCE_NAME-k8saas-reader-cluster-role will have Viewer
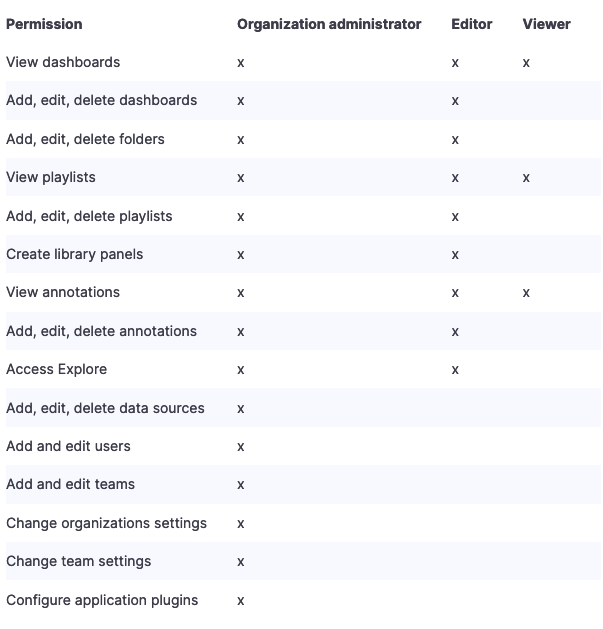
You can use the image bellow as a reference to understand the rights given to each of these roles.
Known Limitation: To provide access to grafana without providing access to your K8SaaS Cluster you will need to open a ticket on PostiT