Built-in SSO for Thales employees (Oauth2) (Deprecated)
We recommend to use the SSO new generation except if you are using a corporate k8saas instance.
Context
k8saas is a Thales service. A significant part of our workloads are dedicated to thales employees. To restrict the accesses we usually use an App Registration in Azure Active Directory. To avoid to many requests to the IT support, k8saas provides a generic App Registration to both identify and authorize Thales Employees to access to the application hosted in k8saas.
Basically, the All in one application publication service feature works like:
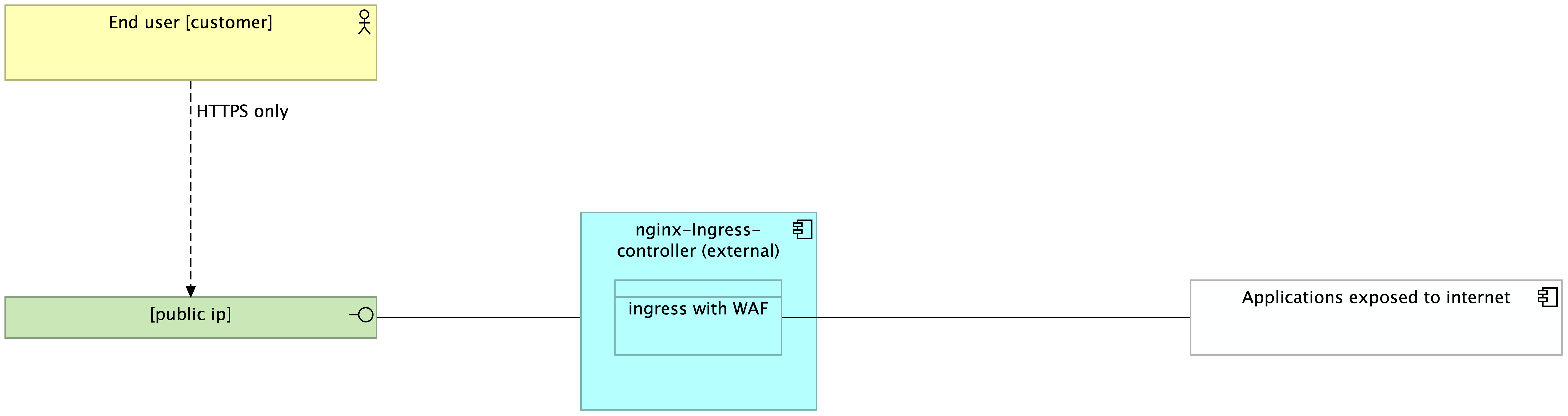
The flow is:
- the user access to the domain
- the ingress controller binds the domain with an ingress configuration
- the ingress controller provide a valid TLS certificate based on the ingress configuration
- then the ingress route the request to the application using a kubernetes service
The Built-in SSO works like:
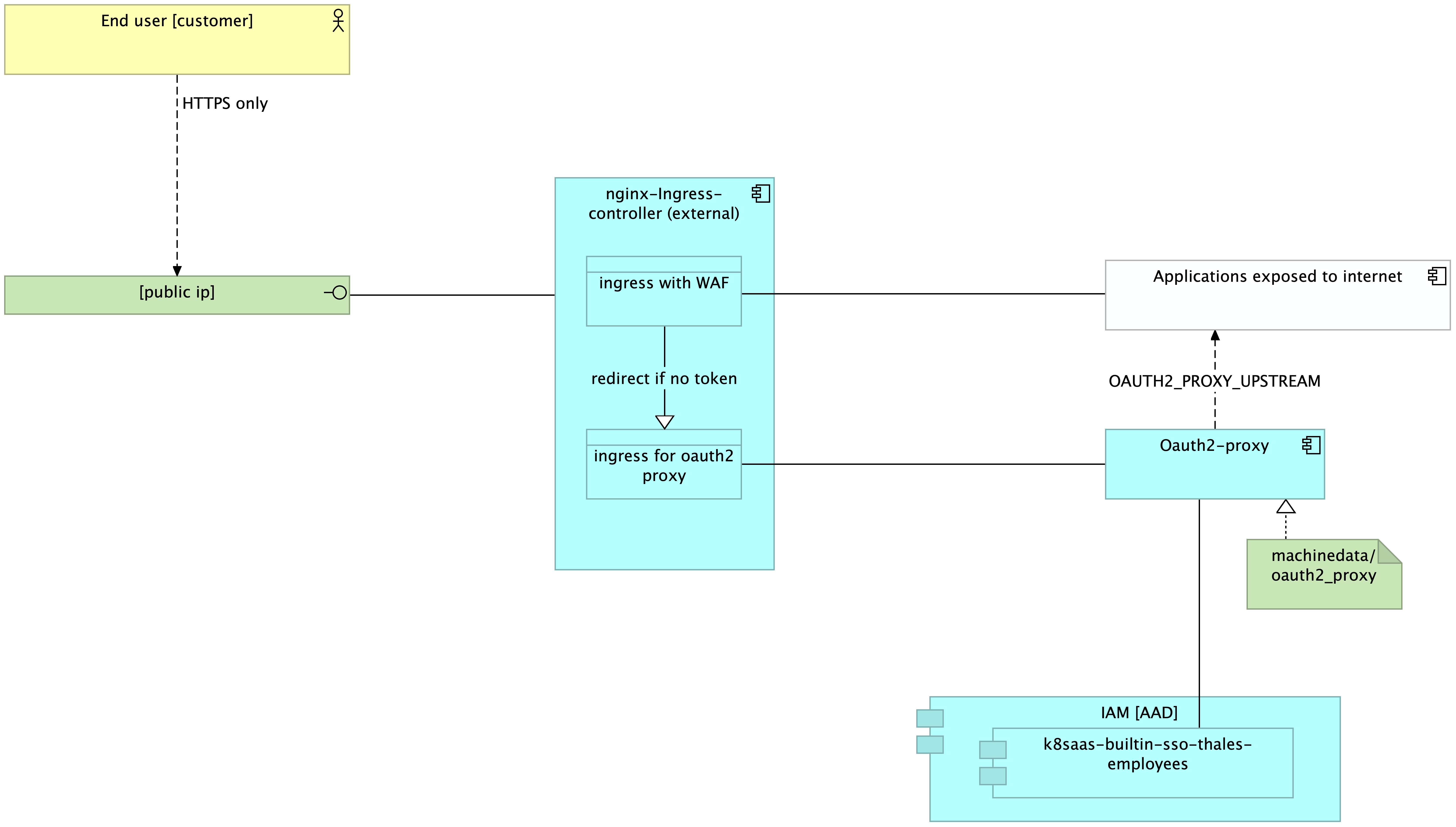
The flow is: For the first request:
- the user access to the domain
- the ingress controller binds the domain with an ingress configuration
- because there is no token, the ingress redirect the user to the oauth 2 proxy
- the user now is invited to provide his credentials
- then the user is redirect to the real application using OAUTH2_PROXY_UPSTREAM
For the second request:
- the user follows the simple stream presented earlier with a validation of the token at any request
The feature is based on dockerhub project
Use case
- After GoToDemo Gate, expose an application to user outside the development team without using a VPN
What to do ?
First, ask for the credentials of the App Registration named "k8saas-builtin-sso-thales-employees" on the TrustNest K8SaaS Service catalog. Please provide to the support team the reply_url that need to be configured in the SSO.
Second, here is an example for explanation purpose:
apiVersion: apps/v1
kind: Deployment
metadata:
name: oauth2-proxy
spec:
replicas: 1
selector:
matchLabels:
app: oauth2-proxy
template:
metadata:
labels:
app: oauth2-proxy
spec:
containers:
- env:
- name: OAUTH2_PROXY_PROVIDER
value: azure
- name: OAUTH2_PROXY_AZURE_TENANT
value: <OAUTH2_PROXY_AZURE_TENANT_ID>
- name: OAUTH2_PROXY_CLIENT_ID
value: <OAUTH2_PROXY_APP_ID>
- name: OAUTH2_PROXY_CLIENT_SECRET
value: <OAUTH2_PROXY_CLIENT_SECRET>
- name: OAUTH2_PROXY_HTTP_ADDRESS
value: "0.0.0.0:4180"
- name: OAUTH2_PROXY_UPSTREAM
value: "http://<SERVICE_NAME>.<NAMESPACE>.svc.cluster.local"
image: machinedata/oauth2_proxy:latest
imagePullPolicy: IfNotPresent
name: oauth2-proxy
ports:
- containerPort: 4180
protocol: TCP
---
apiVersion: v1
kind: Service
metadata:
labels:
k8s-app: oauth2-proxy
name: oauth2-proxy
spec:
ports:
- name: http
port: 4180
protocol: TCP
targetPort: 4180
selector:
app: oauth2-proxy
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: oauth2-proxy
annotations:
cert-manager.io/cluster-issuer: "letsencrypt-prod"
nginx.ingress.kubernetes.io/enable-modsecurity: "true"
nginx.ingress.kubernetes.io/modsecurity-snippet: |
SecRuleEngine On
SecAuditLog /dev/stdout
Include /etc/nginx/owasp-modsecurity-crs/nginx-modsecurity.conf
spec:
ingressClassName: nginx
rules:
- host: <APP_URL>
http:
paths:
- path: /oauth2
pathType: Prefix
backend:
service:
name: oauth2-proxy
port:
number: 4180
tls:
- hosts:
- <APP_URL>
secretName: oauth2-proxy-tls
Now, update the following variables:
<OAUTH2_PROXY_AZURE_TENANT_ID>by the info provided by the support team<OAUTH2_PROXY_APP_ID>by the info provided by the support team<OAUTH2_PROXY_CLIENT_SECRET>by the info provided by the support team<SERVICE_NAME>must be replaced by the name of the kubernetes services bind to your application
kubectl get services -n <NAMESPACE>
<NAMESPACE>must be replaced by the namespace where the service is deployed<APP_URL>the same URL has the default ingress of your application
Then, apply this file in your namespace
kubectl apply -f oauth2-proxy-kubernetes.yml -n <NAMESPACE>
Once done, you should add the following 2 lines in the default ingress configuration, section metadata.annotations:
nginx.ingress.kubernetes.io/auth-url: "https://$host/oauth2/auth"
nginx.ingress.kubernetes.io/auth-signin: "https://$host/oauth2/start?rd=$escaped_request_uri"
Redeploy it, you should be able to use the generic thales sso, try to access to your URL !
HOWTO
Use internal ingress rather than the public one ?
Update the ingress class of both ingresses. Here is the field to set:
spec:
ingressClassName: nginx
TROUBLESHOOTING
Unable to protect 2 different applications in the same namespace using this mechanism
The configuration in example does not work for multiple application, because of the OAUTH2_PROXY_UPSTREAM settings. To put this mechanism in place, we recommend to adapt the naming convention using the name of the application everywhere.
For example:
apiVersion: apps/v1
kind: Deployment
metadata:
name: oauth2-proxy-app1
spec:
replicas: 1
selector:
matchLabels:
app: oauth2-proxy-app1
template:
metadata:
labels:
app: oauth2-proxy-app1
spec:
containers:
- env:
- name: OAUTH2_PROXY_PROVIDER
value: azure
- name: OAUTH2_PROXY_AZURE_TENANT
value: <OAUTH2_PROXY_AZURE_TENANT_ID>
- name: OAUTH2_PROXY_CLIENT_ID
value: <OAUTH2_PROXY_APP_ID>
- name: OAUTH2_PROXY_CLIENT_SECRET
value: <OAUTH2_PROXY_CLIENT_SECRET>
- name: OAUTH2_PROXY_HTTP_ADDRESS
value: "0.0.0.0:4180"
- name: OAUTH2_PROXY_UPSTREAM
value: "http://<SERVICE_NAME>.<NAMESPACE>.svc.cluster.local"
image: machinedata/oauth2_proxy:latest
imagePullPolicy: IfNotPresent
name: oauth2-proxy-app1
ports:
- containerPort: 4180
protocol: TCP
---
apiVersion: v1
kind: Service
metadata:
labels:
k8s-app: oauth2-proxy-app1
name: oauth2-proxy-app1
spec:
ports:
- name: http
port: 4180
protocol: TCP
targetPort: 4180
selector:
app: oauth2-proxy-app1
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: oauth2-proxy-app1
annotations:
cert-manager.io/cluster-issuer: "letsencrypt-prod"
nginx.ingress.kubernetes.io/enable-modsecurity: "true"
nginx.ingress.kubernetes.io/modsecurity-snippet: |
SecRuleEngine On
SecAuditLog /dev/stdout
Include /etc/nginx/owasp-modsecurity-crs/nginx-modsecurity.conf
spec:
ingressClassName: nginx
rules:
- host: <APP_URL>
http:
paths:
- path: /oauth2
pathType: Prefix
backend:
service:
name: oauth2-proxy-app1
port:
number: 4180
tls:
- hosts:
- <APP_URL>
secretName: oauth2-proxy-app1-tls
Next step
- Use your own app registration ! Ask the IT Team to do so using the TrustNest Support Platforms
- Look at the SSO new generation easier to configure !