Managed Network Security Groups
Azure Kubernetes Services is used to run workloads and expose services (Human-Machine Interface / User Interface and/or Application Programing Interface). When publishing interfaces to internet, it's very common to have few attackers that perform scans our services to identify potential vulnerabilities. To avoid security breach, the Trustnest platform security policy recommends limiting the service exposition to TCP/443, with security mechanisms that analyses the content of the queries (such as a WAF - Web Application Firewall) and a blacklist IP that blocks malicious IP provided by Trustnest threat intelligence service.
To make the developer journey easier, k8saas provides a default configured firewall following the cloud security best practices.
The firewall used is based on Azure Network Security Group
Synthesis of the rules:
Inbound:
- HTTPS/HTTP is allowed from anywhere (including internet)
- All others ports are blocked from internet (especially SSH/RDP/FTP/FTPS)
- All communication in the cluster are allowed (pod to pod communications)
Outbound:
- All ports are allowed to internet (except these listed in the following rule)
- SSH/RDP/FTP/FTPS are blocked to internet
- All communication in the cluster are allowed (pod to pod communications)
Use cases
- Expose a Human-Machine Interface (HMI) to users - TCP:443
- Expose a Application Programming Interface (API) to third party system - TCP:443
HOWTO
How to enable this pre-configured firewall ?
By default, cluster has the only HTTPS open and malicious IPs have been blocked. No action is required by customer.
How to request an exception
This section describes the process to get specific NSG access configuration.
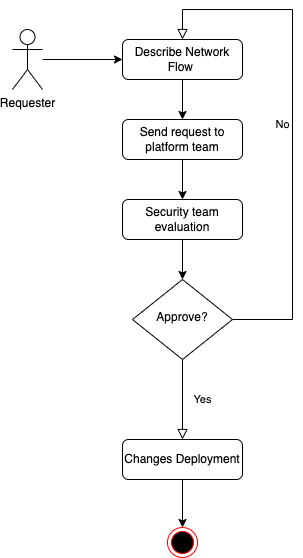
- (Requester) Describe the network flow
- Functional explanation of the flow
- From/to
- Why?
- (Requester) Send a request with all the flow information on the TrustNestK8SaaS Service Catalog
- (plafform team) Security team approbation The request will be reviewed by the security team and approved
- (plafform team) Exception deployment Once security team has approved the network access access, the change will be applied to the customer cluster
How restrict access to authorized IPs only
This case will restrict HTTPS and cluster accesses by only a list of authorized IPs.
Open a ticket on the TrustNestK8SaaS Service Catalog .
Note: You have also the possibility to enable a light whitelisting following the All in one application publication service / section "Configure a whitelist".
Technical description / architecture
Architecture
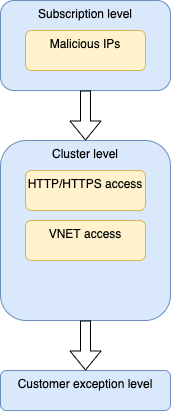
The following diagram show the 3 different level of firewall rules applied on AKS cluster.
- Subscription level The first level is applied for the entire subcription, it consists to block Inbound and Outbound connections from Malicious IPs. These Malicious IPs are suspicious IPs reported by the security team.
- Cluster level The level is applied by cluster, it consists to configure http/https and vnet access. These rules are uniform between cluster.
- Customer exception level contains rule modifications specific accesses. Any configuration access at this level is an exception and requires approbation by the security team
Default NSG rules
| Level | Priority | Name | Port | Direction | Access | Source | Destination |
|---|---|---|---|---|---|---|---|
| Cluster | 100 | k8saas_backlisted_ips_rule_inbound [legacy] | * | Inbound | Deny | [Malicious IPs] | Any |
| Subcription | 202 | k8saas_nsg_rule_blacklist_ip_inbound | * | Inbound | Deny | [Malicious IPs] | Any |
| Cluster | 501 | K8saas_HTTP_internet_to_ldb_Inbound | 80 | Inbound | Allow | Internet | Any |
| Cluster | 502 | K8saas_HTTPS_internet_to_ldb_Inbound | 443 | Inbound | Allow | Internet | Any |
| Cluster | 503 | K8saas_HTTP_ldb_to_aks_Inbound | 80 | Inbound | Allow | AzureLoadBalancer | Any |
| Cluster | 504 | K8saas_HTTPS_ldb_to_aks_Inbound | 443 | Inbound | Allow | AzureLoadBalancer | Any |
| Cluster | 1000 | K8saas_AllowVnetInBound | * | Inbound | Allow | VirtualNetwork | VirtualNetwork |
| Cluster | 2000 | K8saas_DenyAll_Inbound | * | Inbound | Deny | Any | Any |
| ---- | ---- | ---- | ---- | ---- | ---- | ---- | ---- |
| Cluster | 100 | k8saas_backlisted_ips_rule_outbound [legacy] | * | Outbound | Deny | Any | [Malicious IPs] |
| Cluster | 101 | k8saas_denyssh_ips_rule_outbound | 22 | Outbound | Deny | Any | Any |
| Cluster | 102 | k8saas_denyrdp_ips_rule_outbound | 3389 | Outbound | Deny | Any | Any |
| Cluster | 103 | k8s_nsg_deny_ftps_connection_rule_outbound | 990 | Outbound | Deny | Any | Any |
| Cluster | 104 | k8s_nsg_deny_ftps_data_rule_outbound | 989 | Outbound | Deny | Any | Any |
| Subcription | 202 | k8saas_nsg_rule_blacklist_ip_outbound | * | Outbound | Deny | Any | [Malicious IPs] |
| Cluster | 500 | K8saas_AllowVnetOutBound | * | Outbound | Allow | VirtualNetwork | VirtualNetwork |
| Cluster | 501 | K8saas_AllowInternet_Outbound | * | Outbound | Allow | Any | Internet |
| Cluster | 2000 | K8saas_DenyAll_Outbound | * | Outbound | Deny | Any | Any |
Next steps
- Protected your services by exposing them internally using the Private Ingress Exposition
- Learn how to expose your application using our Ingress documentation