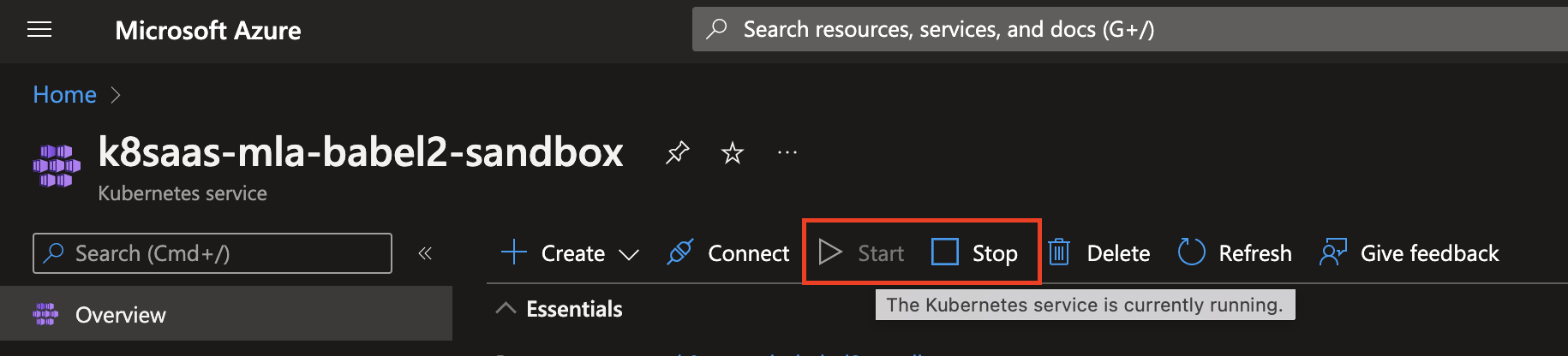
Stop & Start your AKS cluster
Introduction
To reduce the infrastructure cost of your k8saas environment, you can self stop and start your AKS clusters.
Pre requiste
- AKS cluster
- The k8saas-devops-cluster-role must be assigned to you in order to perform stop and start actions on your AKS cluster. Role permission details
How To:
Gitlab Jobs
You will need to request a Service principale/App Registration on postit Here
Once received you will need to add this application to the k8saas-devops-cluster-role of your cluster.
- How to add the permission if not familiar with the process Role permission details
- Or if you want the application to only have the Start-stop capabilities, open a Postit request to have the permissions added to the application for your k8saas cluster.
Before trying to do the operation via Gitlab, we suggest testing the application from your terminal, this way you can confirm the permission are working properly before venturing on the configuration of your automated job:
e.g.
az login --service-principal -u <app-id> -p <password-or-cert> --tenant "737c6905-f186-4bcf-afb3-43e349ee23a3"
az account set --subscription "MVP-TDF-K8SAAS"
az aks start --name k8saas-<instance_name> --resource-group k8saas-<instance_name>
or
az aks stop --name k8saas-<instance_name> --resource-group k8saas-<instance_name>
The following example will only run if it's through a schedule pipeline and will have the start as manual option.
stages:
- stop
- start
variables:
AZURE_CLIENT_ID: "$AZURE_CLIENT_ID"
AZURE_CLIENT_PASSWORD: "$AZURE_CLIENT_PASSWORD"
INSTANCE_NAME: "$INSTANCE_NAME"
AZURE_TENANT_ID: "$TENANTID"
AZURE_SUBSCRIPTION: "MVP-TDF-K8SAAS-TEST" #Replace this by your cluster's subscription name.
stop:
stage: stop
image: mcr.microsoft.com/azure-cli:latest
only:
- schedules
script:
- az login --service-principal -u "$AZURE_CLIENT_ID" -p "$AZURE_CLIENT_PASSWORD" --tenant "$AZURE_TENANT_ID"
- az account set --subscription "$AZURE_SUBSCRIPTION"
- az aks stop --name "k8saas-$INSTANCE_NAME" --resource-group "k8saas-$INSTANCE_NAME"
start:
stage: start
image: mcr.microsoft.com/azure-cli:latest
script:
- az login --service-principal -u "$AZURE_CLIENT_ID" -p "$AZURE_CLIENT_PASSWORD" --tenant "$AZURE_TENANT_ID"
- az account set --subscription "$AZURE_SUBSCRIPTION"
- az aks start --name "k8saas-$INSTANCE_NAME" --resource-group "k8saas-$INSTANCE_NAME"
when: manual
To configure a schedule Pipeline
On gitlab, open your project and browse the side menu for Build>Pipeline Schedules
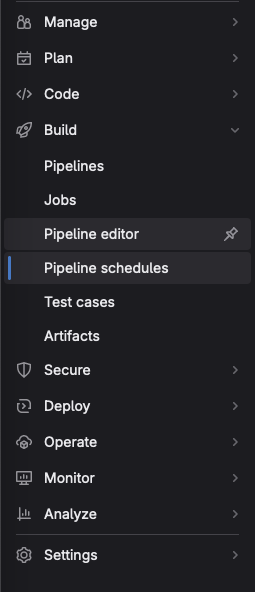
Click New Schedule
Configure your schedule, in this example it will trigger at 7AM EST.
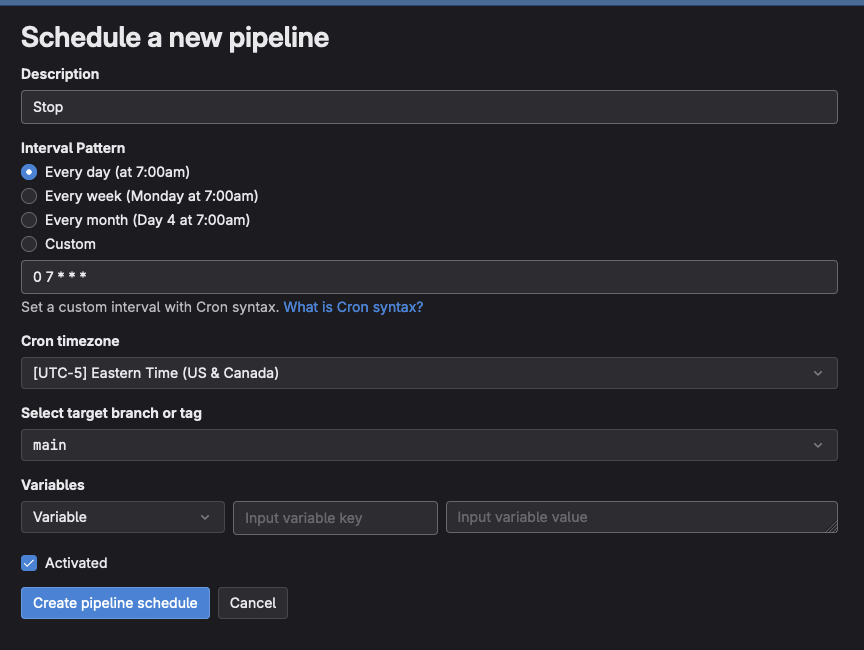
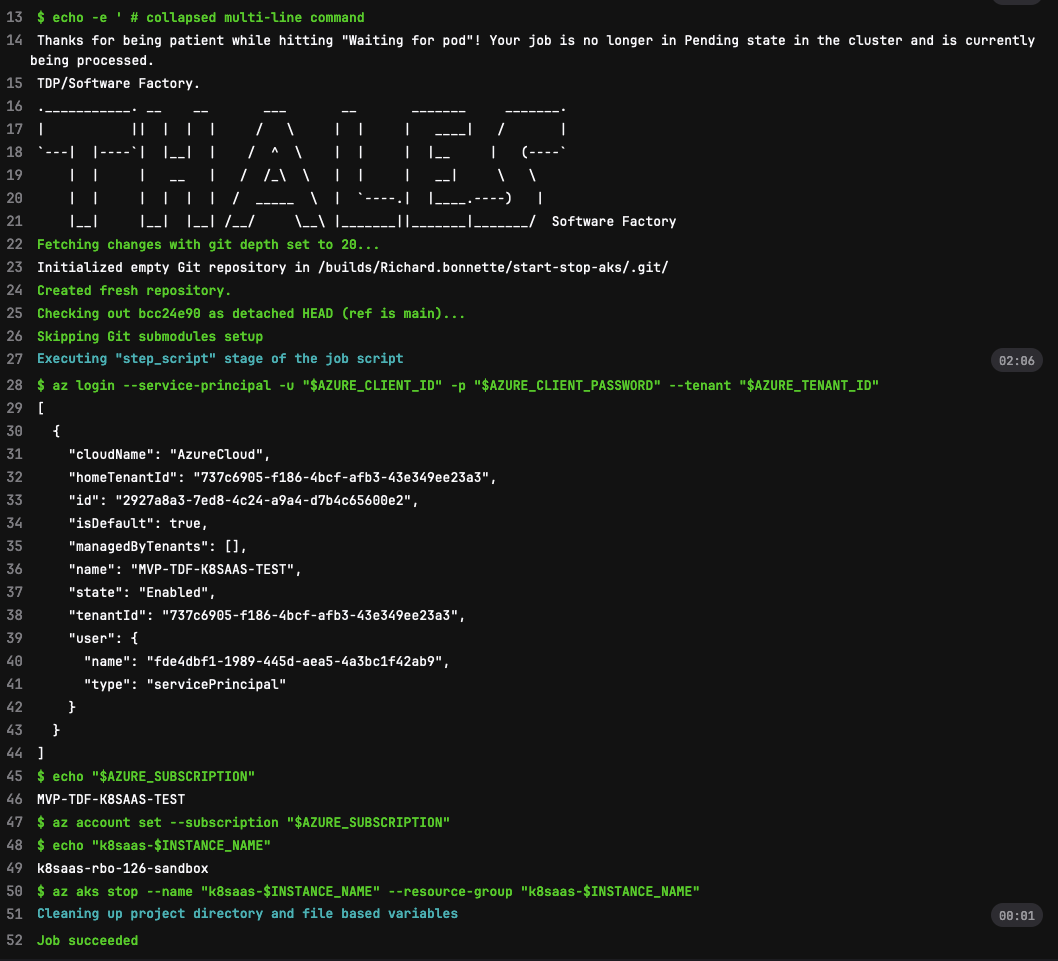
Once done, if you like you can manually trigger the job to test it.
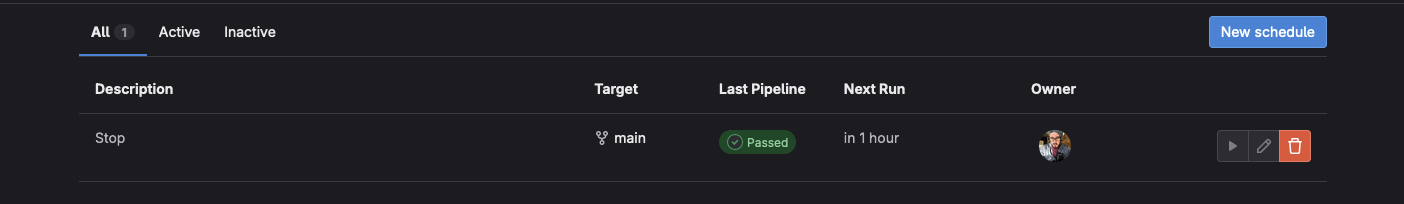
The result should look something similar to this:
If you are using the example above. To Start your cluster, open the latest executed Pipeline
Press the Play button next to the Start Stage.
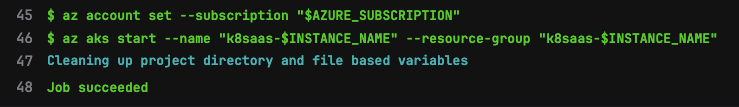
Success!
There's a document by LZ/IAM to use a federated application to run command on gitlab here Using a federated application will let you use the application without the need of providing the application secret, forgoing the need to update the credential regularly.
Manually With Azure CLI
After login in the subscription:
- Start:
$ az aks start --name k8saas-<instance_name> --resource-group k8saas-<instance_name>
- Stop
$ az aks stop --name k8saas-<instance_name> --resource-group k8saas-<instance_name>
- List
$ az aks list --resource-group k8saas-<instance_name>
Through Azure Portal
- Go to AKS service : https://portal.azure.com/#view/HubsExtension/BrowseResource/resourceType/Microsoft.ContainerService%2FmanagedClusters
- Select your cluster
- Click on Start or Stop action