Exposing your corporate add-on application using Thales private domain
Context
You have deployed your application in the C3 perimeter, now you want to be able to access your endpoint from TNAP and/or SWIT Laptop (Thales RIE Network). For this you need to expose your endpoint FQDN. This document will help you to achieve this task.
Network Interconnection with Thales Group Network
All k8saas c3* perimeters are accessible from the Thales RIE.
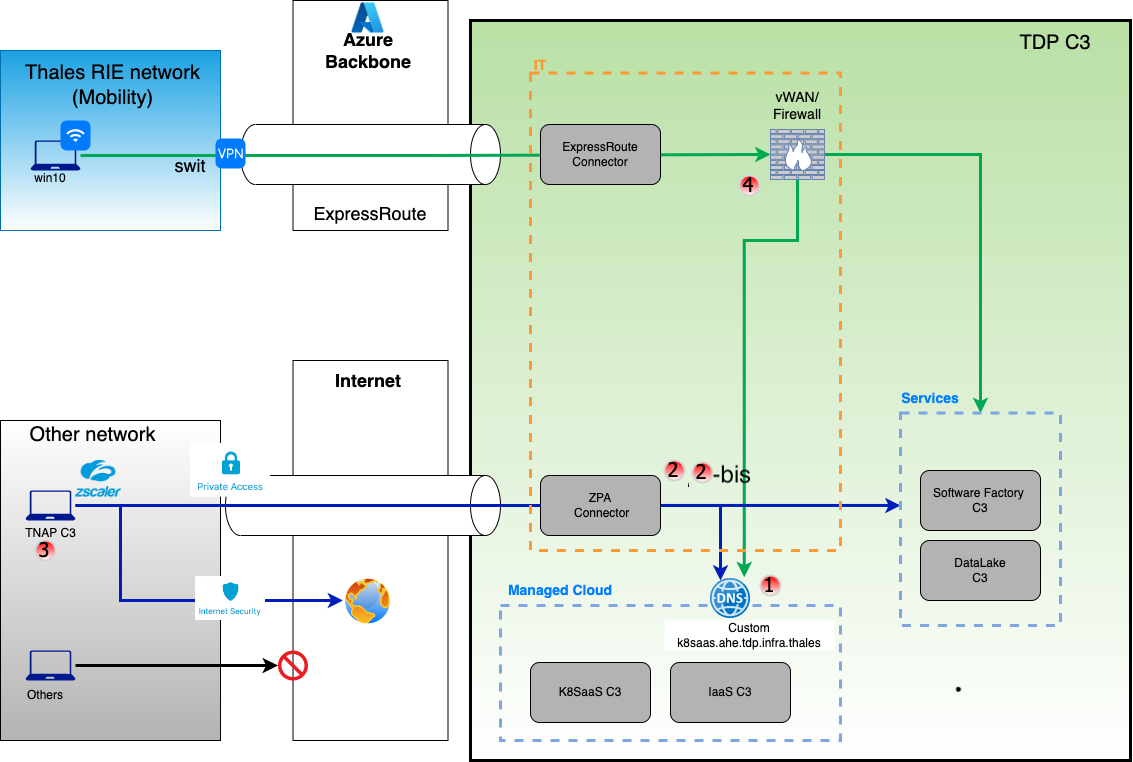
DNS resolution
All k8saas c3* perimeters are able to resolve private Thales DNS from AKS nodes (to pull images from software factory c3) as well as the AKS containers (to interact with the same software factory c3).
HOWTO
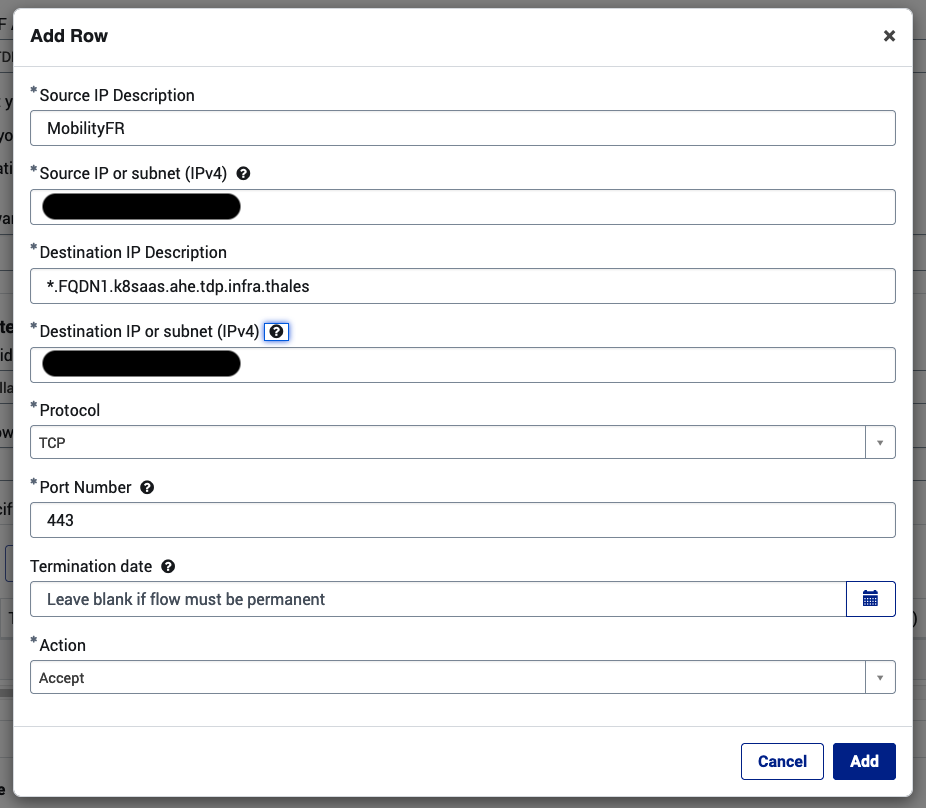
To allow access and present your endpoint to Thales Users, you will need to Open several Postit tickets
1 - Creation of your FQDN in the Custom K8Saas DNS
Please, go to TrustNest K8SaaS Platform & Services General Inquiry with your security partner in copy and with the following information:
- name of your k8saas instance
- IP
- FQDN
Platform & Services General Inquiry
-
What is the aim of your request? Request for improvement(s)
-
What is your query about? Managed Cloud
-
Short description of your request Add Custom DNS entry for our C3 endpoint for k8saas-instancename
-
Description of your request Hello,
Please add the following entries in the C3 DNS to allow the access from the TNAP and/or SWIT laptop. Env: IP URLs k8saas-instancename1: xx.xx.xx.xx *.FQDN1.k8saas.ahe.tdp.infra.thales k8saas-instancename2: xx.xx.xx.xx *.FQDN2.k8saas.ahe.tdp.infra.thales
Thanks
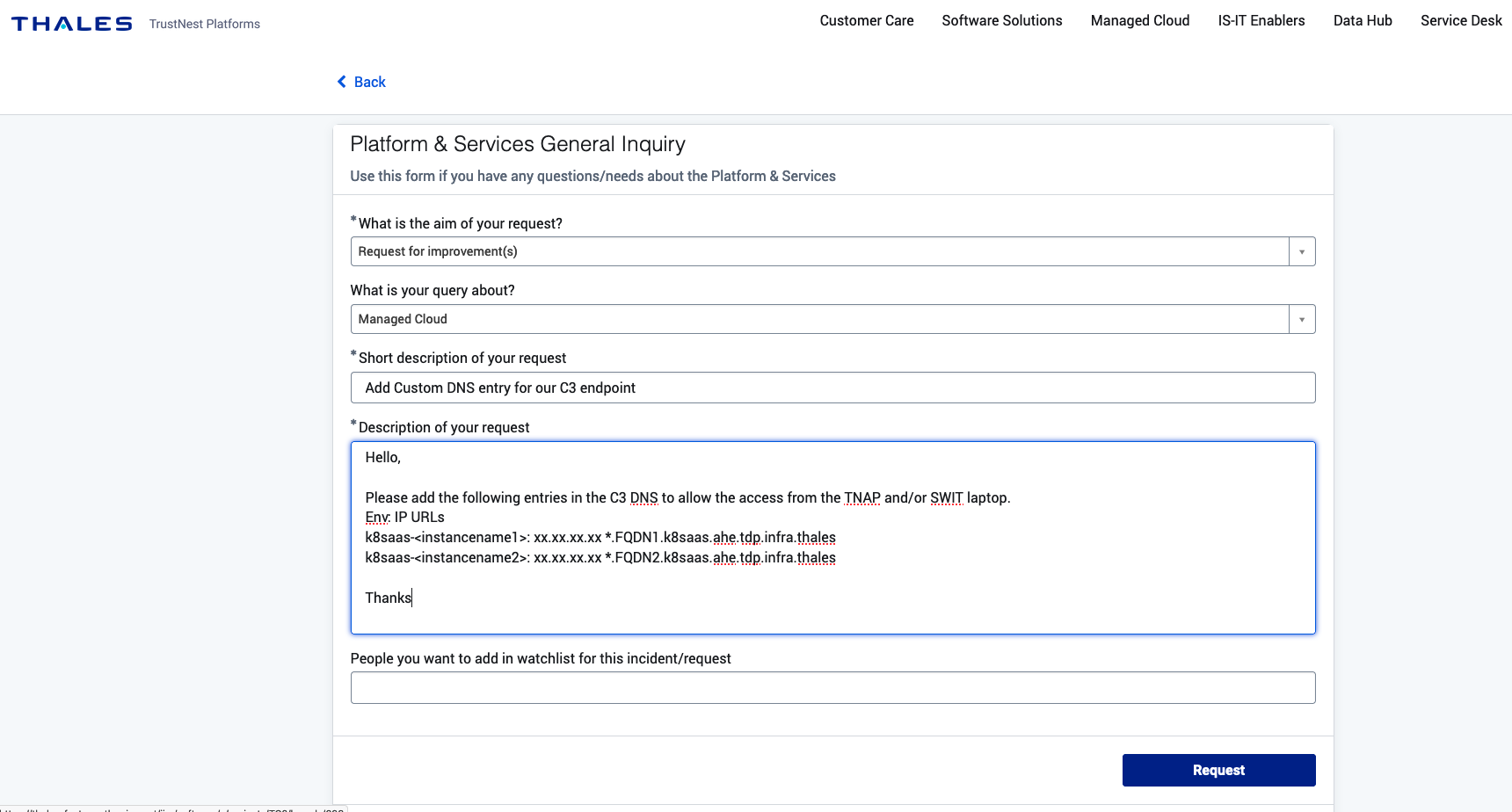
Access to corporate add-on application from TNAP
2 - Create ZPA policy for your FQDN to allow TNAP access
To allow TNAP C3 user to access, we need to update the Zscaler Private Access (ZPA). Please, go to Request a Zscaler Private Access (ZPA) with your security partner in copy and with the following information:
- list of people to access this resource
- FQDN e.g. *.dp-tds-dfna-ks-prod.k8saas.ahe.tdp.infra.thales
Select FQDN Domain: enter e.g. *.dp-tds-dfna-ks-prod.k8saas.ahe.tdp.infra.thales Target port to reach your resources: 80,443
2-Bis - Vnet Peering between your new zone and vWan
To allow the flow to send your access to your new instance, we need to peer the instance vnet with the vWan. To do that please open a Ticket with K8saas team. Please, go to TrustNest Managed CLoud & Virtual Network Peering request
Virtual Network Peering request
- Virtual network ID
- Data classification
- C3
- Service type
- Digital Product
- Additional comment Hello,
Please create a peering between the VNET of my C3 instance 10.XX.XX.XX to TDP-VWAN.
Thanks
3 - Enable TNAP C3 access in ZPA
To allow TNAP C3 user to access, we need to enable the Zscaler Private Access (ZPA). Please, go to TrustNest K8SaaS Platform & Request a Zscaler Private Access (ZPA) with the followings:
Request a Zscaler Private Access (ZPA)
- Operation
- Add
- Data Classification
- C3
- Project name
- Cluster name
- Choose the type of resources to privatise
- FQDN
- Target port to reach your resources
- 443
- Additional Comments Hello,
Please allow TNAP C3 access on the Zscaler Private Access (ZPA) to access *.FQDN1.k8saas.xxx.xxx.xxx.xxx:
aaa@thalesdigital.io bbb@thalesdigital.io ccc@thalesdigital.io
Thanks
Access to corporate add-on application from THALES RIE Network (Mobility)
4 - Enable Access for Thales RIE Network (Mobility)
To allow SWIT user (Mobility) to access, we need to update the ExpressRoute.
Please, go to TrustNest Platform - IS-IT Enablers with the followings:
- TDF Account ID
- Source IP
- Destination IP and FQDN
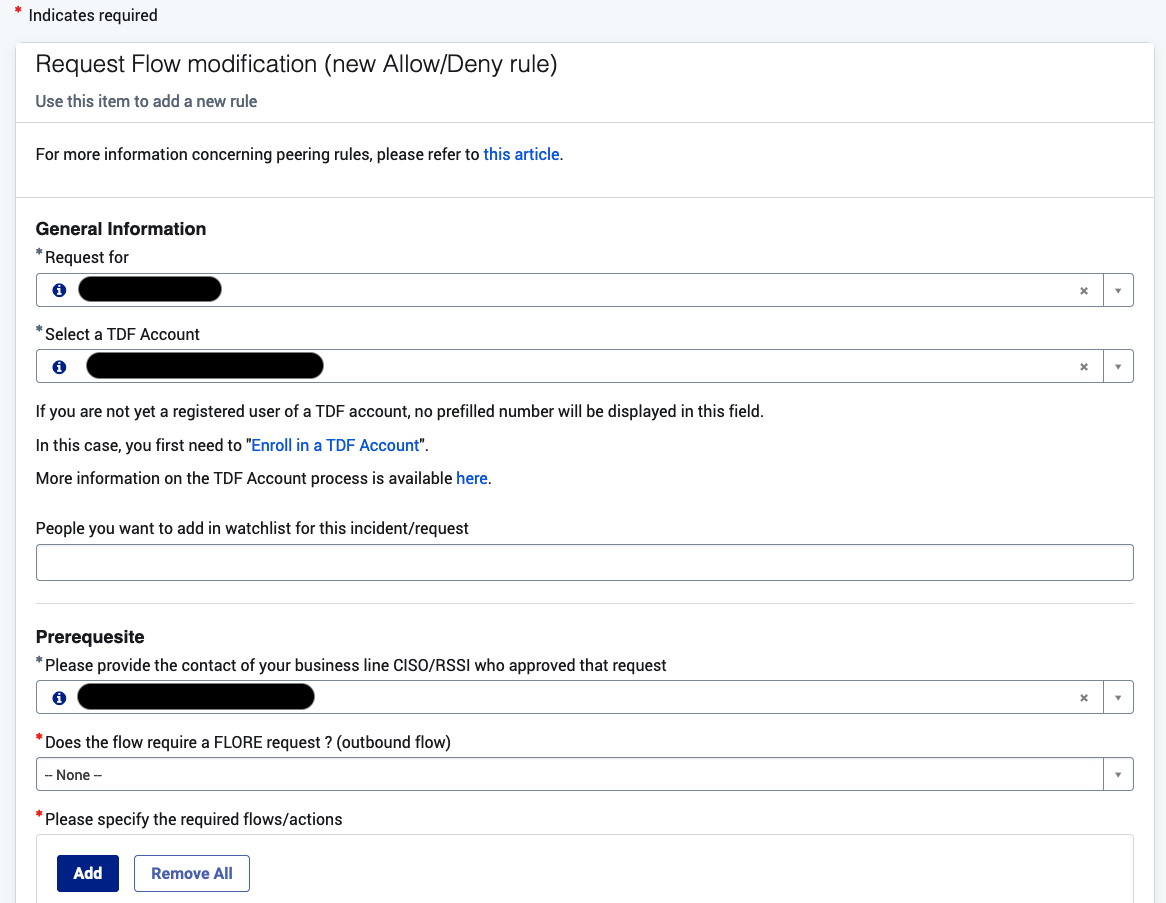
Add a Row for each Flow