Data encryption with Confidential Addon (by Ciphertrust)

Data encryption aways have been and will be a major topic in cybersecurity. And although all data in Azure Disk are encrypted by Azure, it can often be a best practice/requirement to control the encryption keys.
The solution is MCS Confidential Addon : https://blog.mcs.thalesdigital.io/confidential_addon/
Ciphertrust is a data security platform that can generate and rotate encryption keys to be used to encrypt persistent volumes in kubernetes.
All data are encrypted by default by an encryption key managed by Azure, this functionnality add another layer of security on top to ensure that only the entity with access to the encryption key can decrypt the data.
Architecture
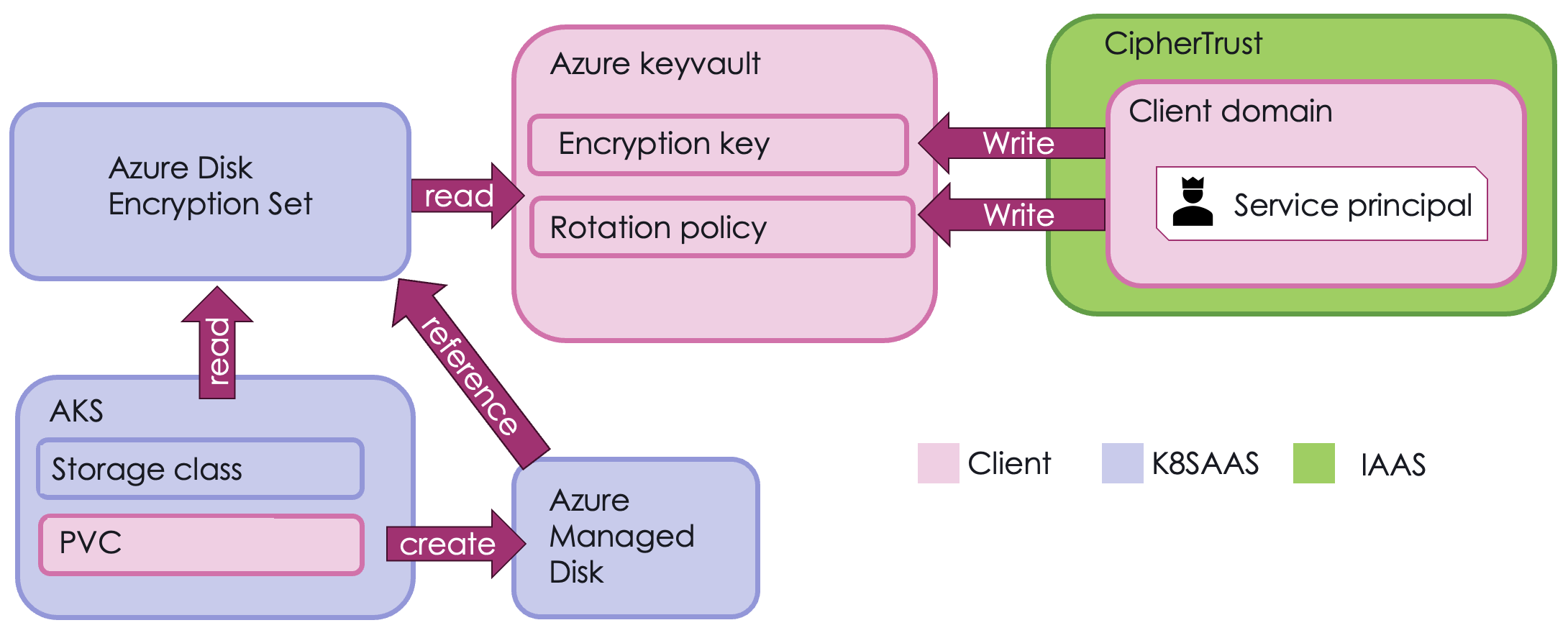
Prerequisites
The prerequisite to use this feature are:
- Own a keyvault with the setting "Purge Protection" enabled
- Own a CipherTrust domain
- Own a service principal used by CipherTrust to connect to Azure
- This service principal should have the "Key Vault Crypto Officer & Key Vault Crypto Service Encryption User" role on the keyvault for keyvault that use 'Azure role-based access control' permission model(recommended).
CipherTrust configuration
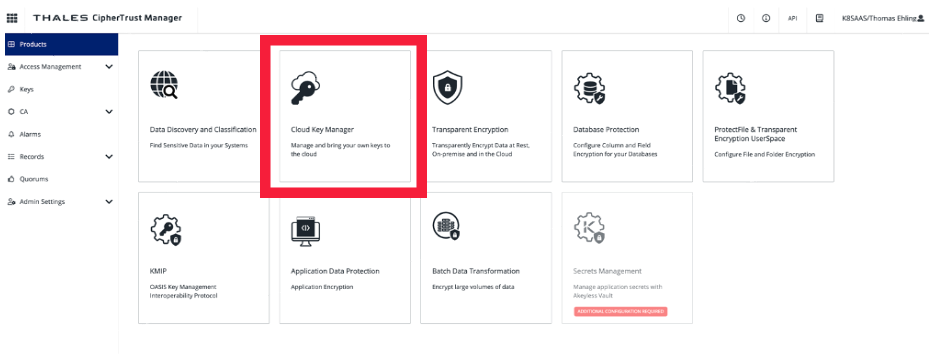
Select on your CipherTrust domain the category "Cloud Key Manager":
First add your keyvault to CipherTrust. Select Containers > Azure Keyvault > Add existing Vault:
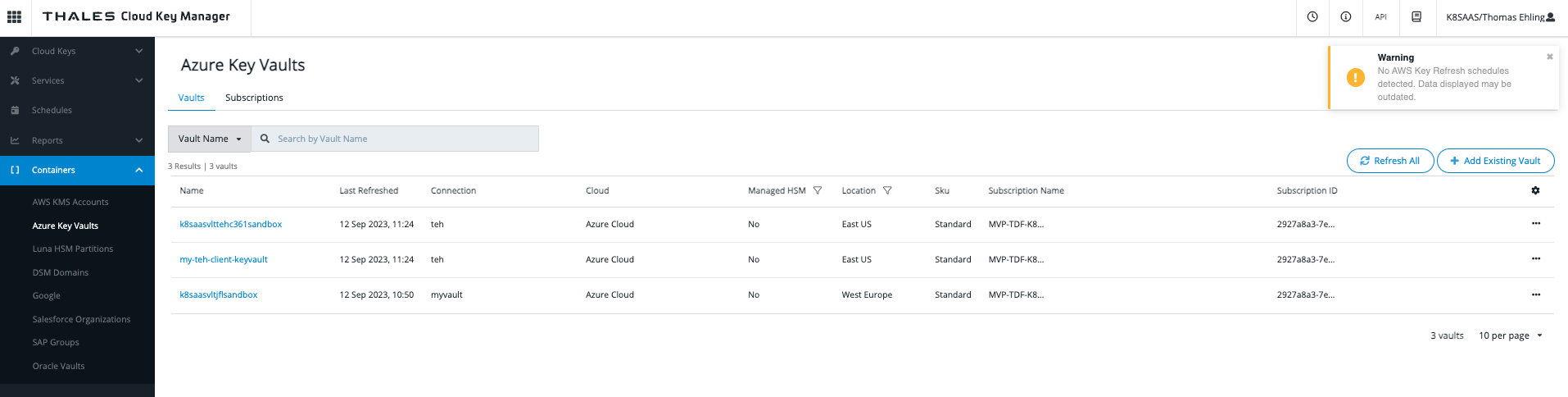
Then choose your Azure connection, subscription and keyvault name.
You should see your keyvault appear on the list.
Once done, create an encryption key in this keyvault. Select Cloud Keys > Azure > Add Key:
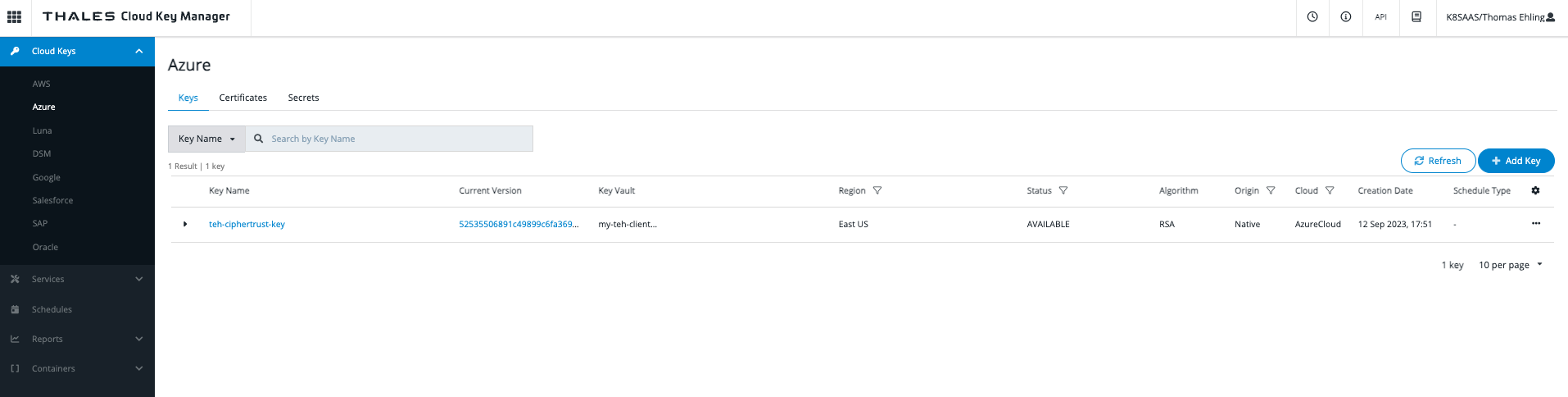
Select "Create/UploadNew Key Material" > "Microsoft Azure (Native)"
Then choose your KEY_NAME, select the keyvault in the drop-down menu and create the key.
Ask for k8saas cluster configuration
Give access to the level 2 Operations team
In order to configure the environement and create the diskEncryptionSet, the level 2 team needs to have access to your keyvault.
In your the Azure Portal, go to your keyvault page, and select Access control (IAM) > + Add > Add role assignment.
On the Role panel, select the role Key Vault Crypto Service Encryption User.
On the Members panel select User, Group or service Principal > Select Members > mcs-env-level2
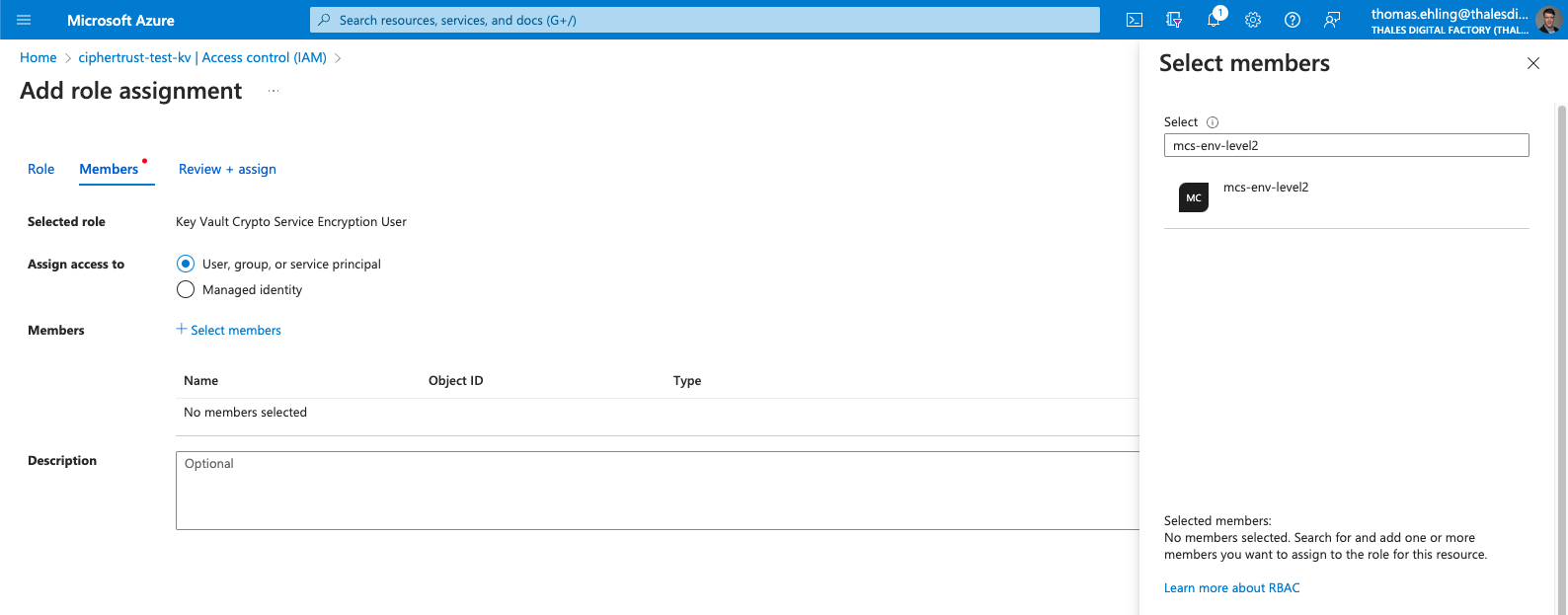
Review and assign.
Send the PostIt request
You should gather the following informations :
- K8saas kubernetes cluster name = name of your cluster
- K8saass kubernetes cluster Subscription ID = id of your cluster's subscription
- Your Azure keyvault Name = name of your keyvault
- Your Azure keyvault subscription ID = subscription id of your keyvault
- Your Azure keyvault resource group name = name of your keyvault's resource group
- Your CipherTrust encryption key name = name of the encryption key generated by ciphertrust in your keyvault
And open a Postit ticket to the K8saas team: POSTIT LINK
DiskEncryptionSet rights on keyvault
To proceed further you need the DiskEncryptionSet ID provided by the Service team once the postit ticket is completed. The next steps will require the DiskEncryptionSet id.
The DiskEncryptionSet have been created and peered to the k8saas cluster. All that is missing is for it to have access to your Azure keyvault's encryption key.
In your the Azure Portal, go to your keyvault page, and select Access control (IAM) > + Add > Add role assignment.
On the Role panel, select the role Key Vault Crypto Service Encryption User.
On the Members panel select Managed identity > Select Members > Disk Encryption Set > DiskEncryptionSet id:
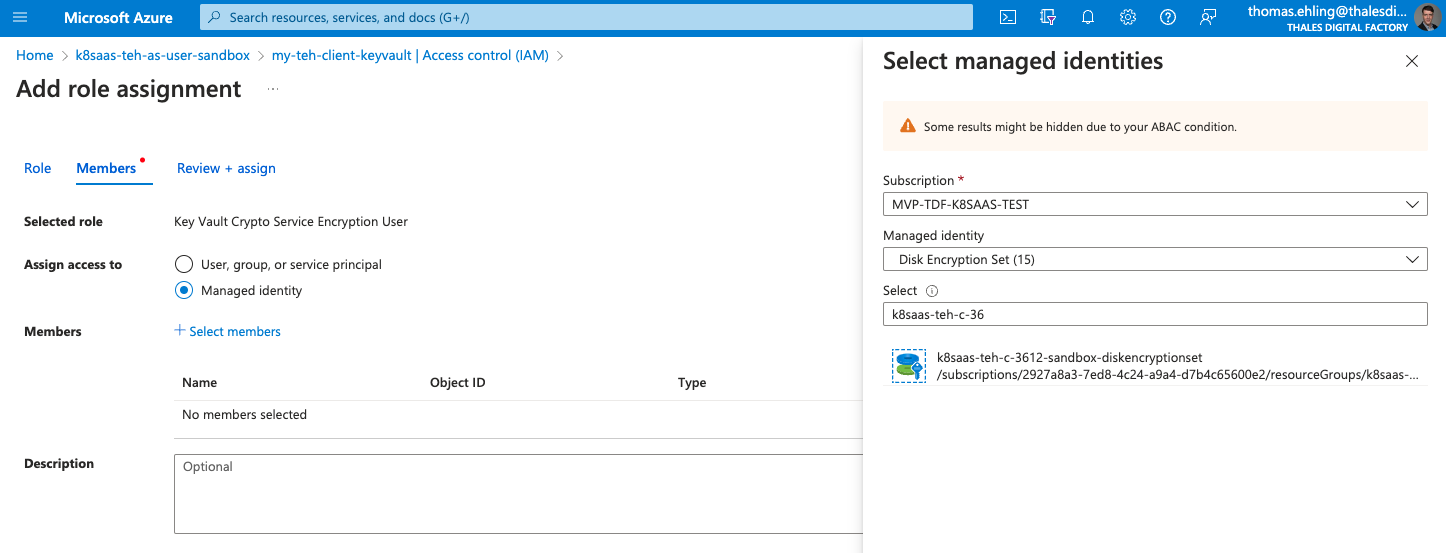
Review and assign.
Now you are all set to encrypt your data ! 🎉
Hello world : how to encrypt a persistent volume
Make sure you are connected to your cluster ! Here is a reminder of the commands to get your credentials:
az account set --subscription $SUBSCRIPTION_ID
az aks get-credentials -n "k8saas-$INSTANCE_NAME" -g "k8saas-$INSTANCE_NAME"
kubelogin convert-kubeconfig -l azurecli
Here is a command to deploy:
- A PersistentVolumeClaim that uses the storage class ciphertrust-storageclass (List somewhere storage class that can be used with cipherytrust, link to storage class ./persistency.md ).
- A pod running an ubuntu image, that mount the pvc on the path /mnt/dst
kubectl apply -f - <<EOF
apiVersion: v1
kind: PersistentVolumeClaim
metadata:
name: aks-helloworld-pvc-des
namespace: customer-namespaces
spec:
storageClassName: ciphertrust-storageclass
accessModes:
- ReadWriteOnce
resources:
requests:
storage: 1Gi
---
apiVersion: v1
kind: Pod
metadata:
name: aks-helloworld-pvc-des
namespace: customer-namespaces
annotations:
linkerd.io/inject: disabled
spec:
containers:
- image: ubuntu
name: copypvc
command: [ "/bin/bash", "-c", "--" ]
args: [ "while true; do sleep 30; done;" ]
volumeMounts:
- name: dst
mountPath: /mnt/dst
volumes:
- name: dst
persistentVolumeClaim:
claimName: aks-helloworld-pvc-des
EOF
The most important point here is the selection of the StorageClass in the pvc creation. The StorageClass "ciphertrust-storageclass" is linked to the DiskEncryptionSet that can use your CipherTrust encryption key.
Let's check that the pod and pvc are properly deployed:
kubectl get pod aks-helloworld-pvc-des --namespace customer-namespaces
# NAME READY STATUS RESTARTS AGE
# aks-helloworld-pvc-des 1/1 Running 0 40m
kubectl get PersistentVolumeClaim aks-helloworld-pvc-des --namespace customer-namespaces
# NAME STATUS VOLUME CAPACITY ACCESS MODES STORAGECLASS AGE
# aks-helloworld-pvc-des Bound pvc-e1707906-4801-49d1-af62-7384c4b967b0 1Gi RWO ciphertrust-storageclass 24s
And now for the moment of truth, let's check the persistent volume that have been created !
On the last query result, under the colum VOLUME, you can see the name of the PersistentVolume bound to your PersistentVolumeClaim. In my example it's pvc-e1707906-4801-49d1-af62-7384c4b967b0.
Use kubectl describe to display the PersistentVolume settings:
kubectl describe PersistentVolume pvc-e1707906-4801-49d1-af62-7384c4b967b0
The output should look like:
Name: pvc-e1707906-4801-49d1-af62-7384c4b967b0
Labels: <none>
Annotations: pv.kubernetes.io/provisioned-by: disk.csi.azure.com
volume.kubernetes.io/provisioner-deletion-secret-name:
volume.kubernetes.io/provisioner-deletion-secret-namespace:
Finalizers: [kubernetes.io/pv-protection external-attacher/disk-csi-azure-com]
StorageClass: ciphertrust-storageclass
Status: Bound
Claim: customer-namespaces/aks-helloworld-pvc-des
Reclaim Policy: Delete
Access Modes: RWO
VolumeMode: Filesystem
Capacity: 1Gi
Node Affinity:
Required Terms:
Term 0: topology.disk.csi.azure.com/zone in [eastus-2]
Message:
Source:
Type: CSI (a Container Storage Interface (CSI) volume source)
Driver: disk.csi.azure.com
FSType:
VolumeHandle: /subscriptions/xxxx-xxxx-xxxx-xxxx/resourceGroups/mycluster-node/providers/Microsoft.Compute/disks/pvc-e1707906-4801-49d1-af62-7384c4b967b0
ReadOnly: false
VolumeAttributes: csi.storage.k8s.io/pv/name=pvc-e1707906-4801-49d1-af62-7384c4b967b0
csi.storage.k8s.io/pvc/name=aks-helloworld-pvc-des
csi.storage.k8s.io/pvc/namespace=customer-namespaces
diskEncryptionSetID=/subscriptions/xxxx-xxxx-xxxx-xxxx/resourceGroups/mycluster/providers/Microsoft.Compute...
kind=Managed
requestedsizegib=1
skuname=StandardSSD_LRS
storage.kubernetes.io/csiProvisionerIdentity=1695185692857-8957-disk.csi.azure.com
Events: <none>
And in the Source.VolumeAttributes you can see the diskEncryptionSetID !
Congrats, your data are encrypted !
Key rotation
In your CipherTrust Domain you can either do a on-shot rotatation of a target key or set up a schedule.
Tip! After rotating your encryption key, you can go check the new version in value of the key in your keyvault>
One-shot rotation
In CipherTrust, you can select your key and choose the option,
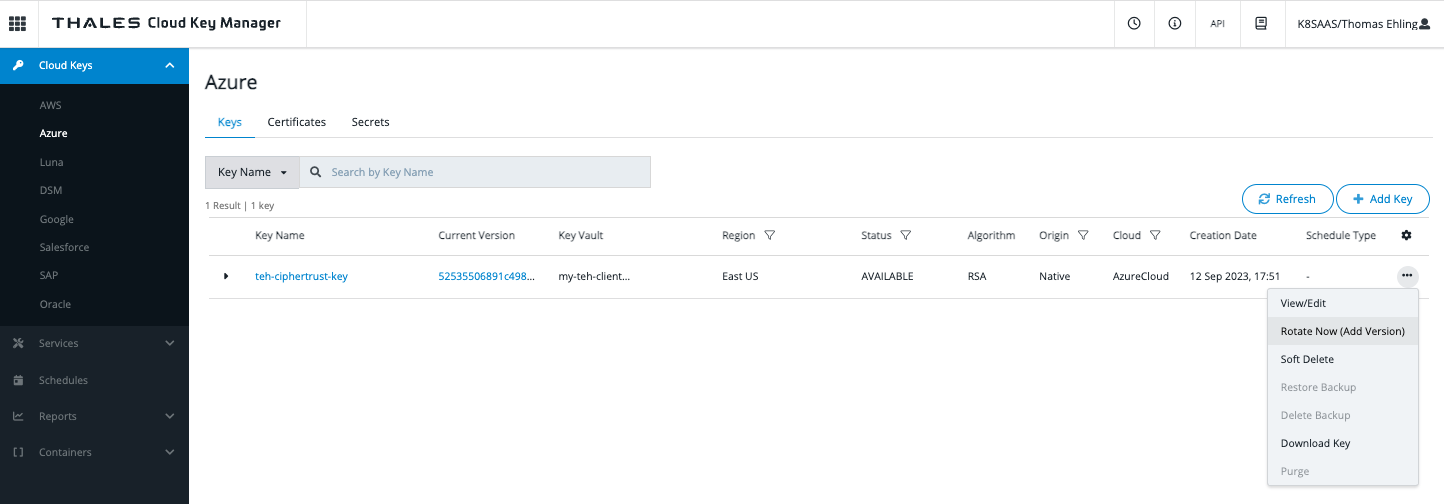
Schedule
Schedules allows you to plain a daily or weekly rotation of your encryption keys.
In the Cloud Key Manager section, select the menu blade Schedules. Click on +Add Schedule. Select Key Rotation. Configure the rotation as you please.
Once created and the schedule running, you can always select it to see the history of the rotation operations.
Backup and restore

At k8saas, making sure your data is backed up and can be restore is one of our top priority !
So we made sure that even with a key rotation schedule active, we'll be able to backup and restore your encrypted persistent volumes (using the DiskEncryptionSet only) !